The Bitcoin Whitepaper simply explained
Published in October 2008, by an individual or a group under the name of Satoshi Nakamoto, the Bitcoin Whitepaper laid the groundwork for a fundamental change in the execution of global payments and the transformation of entire industries in terms of data management.
Bitcoin was introduced as a digital currency to the world in the paper called Bitcoin: A Peer-to-Peer Electronic Cash System
The Bitcoin Whitepaper is only nine pages long and is a proposal for a trustless system of electronic transactions
The Bitcoin network creates a structure for making payments without a trusted third party acting as intermediary
The Bitcoin Whitepaper in simple language attempts to translate complex technological concepts into easy-to-understand terminology
In this article, we are going to provide a simple explanation of the technological fundamentals outlined in the Bitcoin Whitepaper.
The Bitcoin Whitepaper was originally published on the 31st of October, 2008 by an individual or a group of people that called themselves Satoshi Nakamoto in a cryptography mailing list on a platform called Metzdowd. Wild theories and myths surround the actual identity of the creator(s) of Bitcoin - a number of individuals known in the world of cryptocurrencies have claimed to be Satoshi Nakamoto or to know them.
The concept behind Bitcoin is based on cryptography, the study of secure communication technologies and development of protocols preventing the public or third parties from reading private information.
The Abstract
The opener on the first page of the Bitcoin Whitepaper is the abstract of the publication containing a summary that describes the content and purpose of the whitepaper.
Fundamentally, the purpose of Bitcoin is developing computer technology for enabling multiple parties to send payments online directly to each other (“peer-to-peer cash system”) without requiring a financial institution such as a bank. First and foremost it goes without saying that the underlying system for such transactions would need to meet a number of security requirements.
As the proposed transaction is to be cashless and be executed online, the problem of double spending would need to be addressed. Double spending is the potential weakness in a digital cash system - the possibility that the same unit of value (the token) could be spent twice if someone duplicates or falsifies a token.
The prerequisites for this type of decentralised cash system to work are
Cooperation between the parties running the system (network structure)
Ensuring that previous records can never be changed (immutability) and
Agreement on the validity of transactions according to certain rules (consensus)
In other words: all parties need to agree on rules and cooperate in line with those rules while ensuring that records are valid according to these agreed rules as well as immutable.
Introduction - where did Bitcoin come from?
The introductory paragraph of the Bitcoin Whitepaper outlines why the creator thinks that a trustless cash system is needed in the first place. The main reason stated is that traditional payment systems used in commercial settings operating via financial institutions such as banks have a number of flaws.
For one, traditional payments often involve high transaction and mediation costs that may arise if there is a dispute about a transaction, for instance, if a transaction needs to be reversed.
Secondly, traditional payment systems are prone to fraud and thirdly, they always require a trusted third party. The Bitcoin Whitepaper proposes a system in which third parties, if any, such as escrow services for the primary transacting parties, can easily be implemented but only if needed, by triggering some type of coded action.
Transactions
An electronic coin is basically a chain consisting of digital signatures. Electronic coins are actually lines of protected computer code which exist in relation to the previous code in line before them. You can’t hold electronic coins in your hands like a traditional currency, they only exist online.
Let’s say an owner of Bitcoin wants to make a transaction. If the owner activates a transaction to transfer the coin to the next owner, this value of bitcoins is broadcasted to the network.
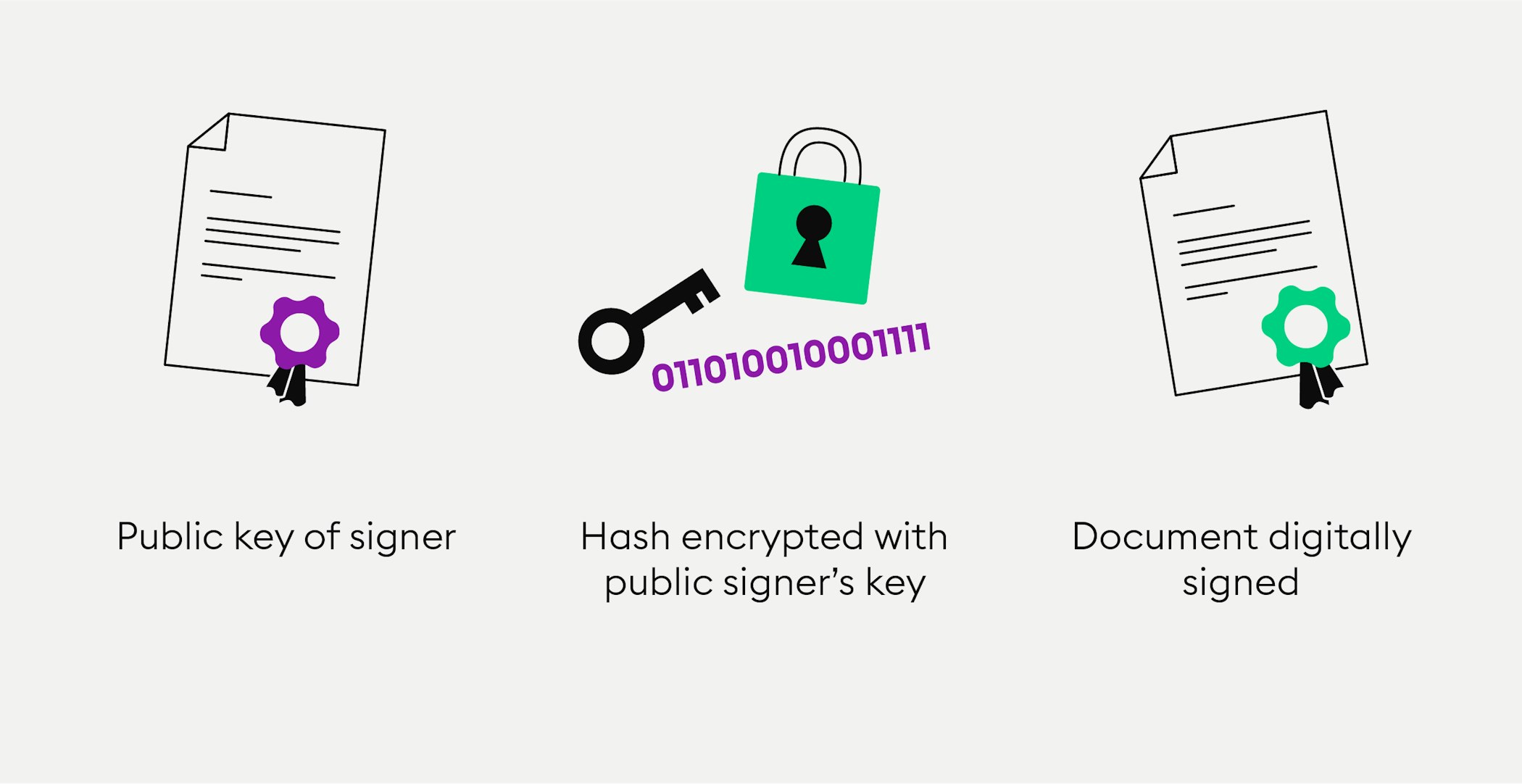
The owner activates the transfer of the coin to the next owner by digitally signing a hash - the unique digital fingerprint - of the previous transaction to encrypt the hash. The encryption behind Bitcoin uses two mathematically related key - a public key and a private key. They are related but not identical.
The public key is needed to encrypt the transaction along with the owner’s private key to create the digital signature - it is similar to a bank account number, while the private key is similar to the access code for a bank account. Therefore the public key is also the address of the recipient, to which the owner wants to send bitcoins.
This information is added to “the end” of the coin.
Naturally, the next owner - the recipient - wants to ensure that the amount sent to them has not been previously spent in an earlier transaction. The only way this can be ensured is by the network agreeing on all transactions made before in the order they have been made.
The valid order of all transactions in the network has to be publicly announced so everyone knows what is valid, and for this, the network needs to have an agreement of rules in place on what is valid.
Each recipient of a transaction wants proof that at the time they received their transaction, the majority of the network agrees that it was the recipient who was the first to receive this transaction and no other recipients have received the same transaction before.
The valid order of all transactions in the network has to be publicly announced so everyone knows what is valid, and for this, the network needs to have an agreement of rules in place on what is valid.
Timestamp Server
This section of the Bitcoin Whitepaper describes how Satoshi Nakamoto proposes the Bitcoin network uses a “distributed timestamp server” to prove in which order transactions were generated. What does this mean?
The Bitcoin network runs on a distributed system of computers. All computer processes in the network run simultaneously on hundreds and thousands of computers - i.e. nodes - located in different countries distributed all over the world. All these computers are connected to each other and anyone with the suitable equipment can set up a computer to join in.
The more computers in the network, the more copies of the records, making the system even more secure. Obviously, it would be close to impossible to simultaneously steal or destroy records from thousands of computers at the same time at once. Therefore, the system is safe as long as the majority of parties operating the computers collectively agree on the longest “chain” of data records - the “valid” blockchain.
Transactions are bundled into blocks containing several transactions and information on the previous block. A timestamp server, a piece of software, adds the timestamp to the hash of a block at the same time on all the hundreds and thousands of computers in the network.
The timestamp provides the proof that the data must obviously have existed at this time, and every timestamp includes the previous timestamp in its hash. This way, a chain is formed with each additional timestamp reinforcing the timestamps before it. Think of the analogy of Russian stacking dolls - a tiny doll inside a larger doll that is inside a larger doll and so on - this is what a Bitcoin transaction looks like.
A timestamp server, a piece of software, adds the timestamp to the hash of a block at the same time on all the hundreds and thousands of computers in the network.
Proof of Work
The fact is that the general time-stamping network suggested by Satoshi in the original Bitcoin Whitepaper was implemented as a peer-to-peer computer network that uses a Proof of Work algorithm in a process known as Bitcoin mining to create a practically unchangeable history of transactions.
In the broadest sense, “Proof of Work” is the solving of a moderately difficult task by a computer user on their computer. This task satisfies certain set requirements and is inherently difficult to execute. Originally, Proof of Work as a method was invented to curb the sending of spam emails. By requiring the sender of emails to perform some small task (“work”) before they could dispatch the email, this was to ensure that no flood of emails would be dispatched.
In the Bitcoin network, this moderately difficult task evolved into solving a cryptographic puzzle. A number of transactions is bundled into a block. A block contains data - an index, the timestamp, a list of the transactions, a proof and the hash of the previous block and further information. A number called a nonce (a “number only used once”) is added to this block to hash it.
The nodes (computers) in the Bitcoin network - the “miners” - now start scanning, testing and discarding millions of nonces each second to find a nonce that meets the target set by the network at the time of the block (the grouping of transactions). They perform this “work” until they find a value that gives the block's hash the required difficulty level: a beginning with a number of zero bits.
Once such a value is found by a miner, it is broadcast to the other nodes in the network, validated and a valid new block has been found and added to the blockchain. No changes can be made to a block, unless the work would be redone.
A block contains data - an index, the timestamp, a list of the transactions, a proof and the hash of the previous block and further information.
You can view all Bitcoin blockchain transactions on Blockexplorer.
New to Bitpanda? Register your account today!
Sign up hereThe speed at which new blocks are added depends on how many participants in the network are working on the validation or how much computing power is used. If too many blocks are generated within an hour, the complexity of the task - the “difficulty” is increased in order to deliberately delay the generation of new blocks.
The valid blockchain is the longest chain with the most computing power invested in this chain by honest network participants.
The Network
The next section of the Bitcoin Whitepaper outlines the transaction process.
A sender dispatches a transaction which is broadcast to all participants in the network (although not all transactions need to reach all nodes). Each participating node gathers the new transactions into a block and tries to find a Proof of Work for it.
Once it is found and it is clear that the transaction has not been previously spent (double-spent), the new block is again broadcast to the Bitcoin network and accepted as valid (or rejected) by the other computers that work on creating a new block using the hash of the last valid block. The longest chain in the blockchain is considered the correct chain.
It may happen that two nodes simultaneously broadcast different versions of the next block into the Bitcoin network. Consequently, other nodes receive either one version first or the other. In this case, the nodes will switch to the longest chain. If a node doesn’t receive a block, it requests the missing block once it realises that it missed it.
Incentive
To encourage computer nodes to participate in the network, Satoshi Nakamoto proposed that nodes supplying computing power should be rewarded if they are the first node to create a block. Users of the Bitcoin network would pay transaction fees, which at a later point would become the sole reward once enough coins were in circulation.
As it would take a huge amount of computing power to defraud the network, nodes are more likely to stay honest than defraud the network. The reason is that investing computing power in mining and generating new coins is more profitable than investing funds into gaining control of the network. Keep in mind that no single company or person is in charge of running the Bitcoin network. Instead, it is operated and verified by a large community of independent computers.
Reclaiming Disk Space
As the Bitcoin blockchain is immutable and can never be changed, it was evident that it would grow in size to reach a point which would require large amounts of memory for storage. In the Bitcoin Whitepaper, it is presumed that a single block header containing no transactions would have an approximate size of about 80 bytes.
To counter the issue of required memory, Satoshi Nakamoto proposed that once a transaction is “buried” under a sufficient number of blocks, the spent transactions before it could be “discarded” to save disk space.
In order to ensure that cryptographic structures - the hashes - would not be broken, the Whitepaper suggests reducing all transactions to a single hash - a root hash - which can efficiently be done by using a Merkle tree.
A Merkle tree or hash tree, named after the scientist Ralph Merkle is a hash-based data structure in cryptography and computer science. This structure assigns data to a key. A simple example of this concept is speed dialing on a phone - each telephone number is assigned to each key in a hash-based structure. In the Bitcoin network, Merkle trees are used for data verification which is efficient because hashes are used instead of a complete information file.
A Merkle tree or hash tree, named after the scientist Ralph Merkle is a hash-based data structure in cryptography and computer science.
Merkle trees typically use a binary-tree structure, meaning each node has at most two child nodes, but a higher level of output can be used as well. The root hash is the upper-most hash in the hash-based data structure and is part of the block header. It ensures which transactions are present.
At the time of the publication of the Bitcoin whitepaper in 2008, it was estimated that at least 4.2MB (megabytes) of memory storage would be needed per year. This was based on the assumption that blocks are generated every ten minutes and each block is equal to 80 bytes. Per hour, this would be equal to 80 multiplied by 6, then multiplied by the cost per day and then per year, i.e. equivalent to 80b multiplied by (6X24) multiplied by 365.
Typical computer systems were sold with 2GB (gigabytes) of RAM in 2008, and at the time Moore's Law was predicting growth of 1.2GB per year, in the Bitcoin Whitepaper it was presumed that storage would not become a problem, even if block headers were to be kept in memory.
Simplified payment verification
Payments in the Bitcoin network can also be verified without a user running a full node in the network by building a Bitcoin implementation that relies on connecting to a trusted full node and downloading only the block headers.
After the download is completed, the client computer verifies the correct connecting of the chain headers and a sufficient level of difficulty to ensure that it is the correct blockchain. Finally, copies of transactions along with a Merkle branch linking them to their respective correct block are provided as proof of inclusion.
As long as honest nodes control a network and you are connecting to a node known to be reliable, this verification is reliable. However, to ensure that transactions are not being fabricated by an attacker on an invalid chain, Satoshi Nakamoto suggests that businesses utilising Bitcoin for frequent payments should run their own nodes for speed and increased security.
In very simple terms, this means you do not need the entire record of the chain to verify a transaction is correct. You only need to download one branch of the merkle tree and check if it has the same root hash.
Combining and Splitting Value
The lessons behind Bitcoin also apply to transactions containing multiple inputs and outputs - similar to how if you need to spend 35 cents, you need to combine 20 cents, 10 cents and 5 cents. In the Bitcoin network, transactions can have multiple inputs and outputs allowing for the splitting and combining of value.
Privacy
Traditional banks ensure the privacy of transactions by limiting information on transactions to the parties involved, including the third-party intermediary. The Bitcoin network on the other hand, announces all transactions publicly. Everyone can see that someone is sending a transaction but the transaction cannot be linked to anyone because no one knows who the acting parties are.
Users identify themselves to the network using a public key but need a private key to access the transaction. Therefore, the Bitcoin Whitepaper recommends to use a new key pair for each transaction in order to ensure that transactions cannot be tracked back or linked to a common owner.
Calculations
Finally, Satoshi Nakamoto wanted to illustrate the unlikelihood that the Bitcoin network would successfully be attacked by fraudsters. This section of the whitepaper contains calculations to show how complicated it would be for an attacker to start a new chain rivaling the valid chain. As honest nodes would not accept a matching transaction, a fraudster would need to race the valid chain and utilise massive amounts of computing power to catch up and the probability that they would ever breakeven is miniscule.
Conclusion
Bitcoin is a peer-to-peer system for trustless, electronic cash transfers that uses Proof of Work to record the public history of transactions and is highly safe against attacks as long as honest nodes control the majority of computing power. The network is made up of nodes that need little coordination and can join and leave at will and only accept valid blocks while rejecting invalid blocks based on a consensus mechanism.
This article does not constitute investment advice, nor is it an offer or invitation to purchase any digital assets.
This article is for general purposes of information only and no representation or warranty, either expressed or implied, is made as to, and no reliance should be placed on, the fairness, accuracy, completeness or correctness of this article or opinions contained herein.
Some statements contained in this article may be of future expectations that are based on our current views and assumptions and involve uncertainties that could cause actual results, performance or events which differ from those statements.
None of the Bitpanda GmbH nor any of its affiliates, advisors or representatives shall have any liability whatsoever arising in connection with this article.
Please note that an investment in digital assets carries risks in addition to the opportunities described above.