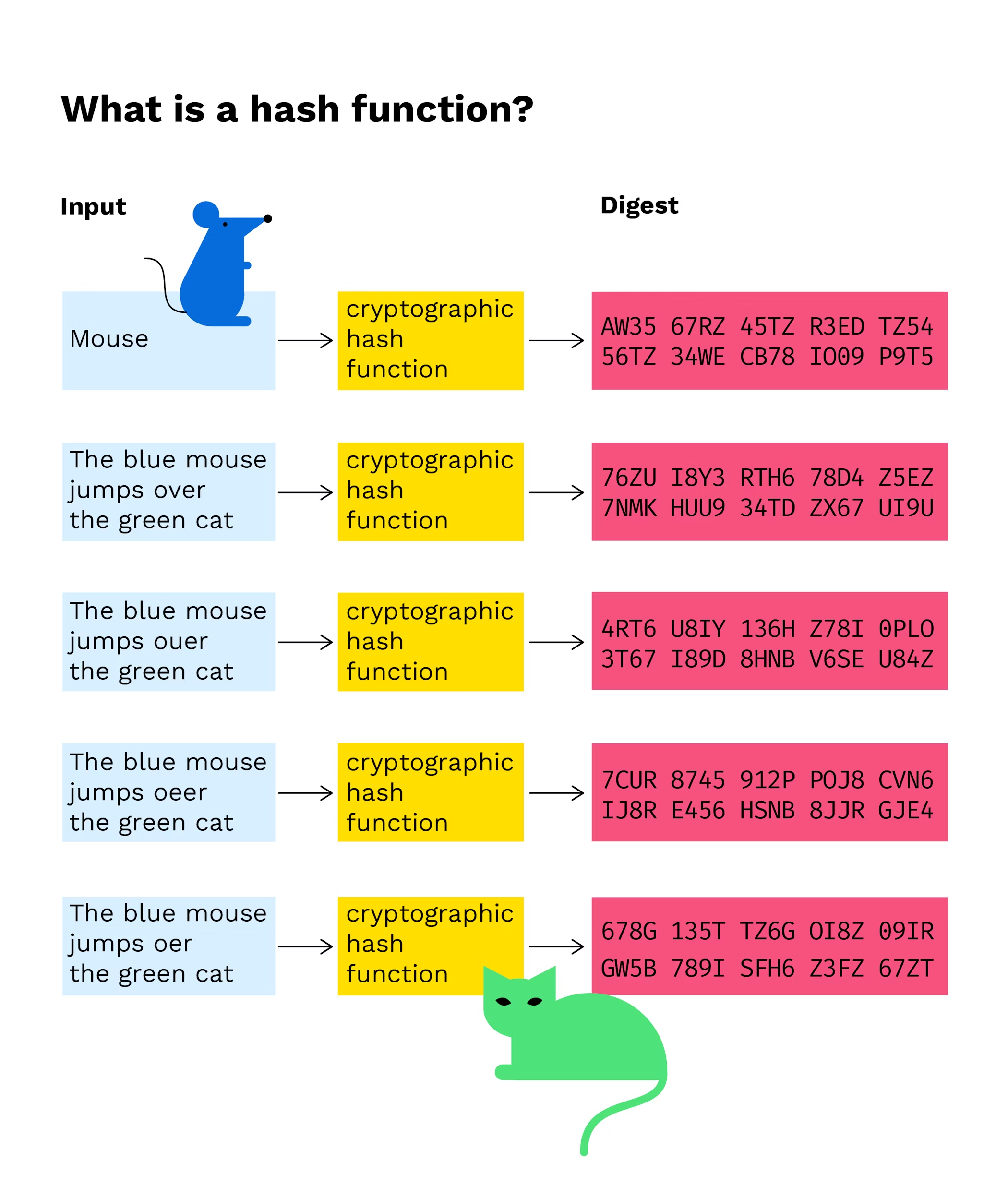
What is a hash function in a blockchain transaction?
Cryptographic hash functions generate a fixed-length character string from data records of any length. A data record can be a word, a sentence, a longer text or an entire file.
A cryptographic hash function is used for security purposes and constitutes the backbone of crypto security
A hash function turns a random input of data (keys) into a string of bytes with a fixed length and structure (hash value)
The hash of a transaction makes it easy to identify transactions on the blockchain
In this article, you are going to learn about the details of hash functions.
What is a hash function?
The Bitcoin network depends on a set of rules called the Proof of Work consensus algorithm. This consensus algorithm is a set of rules that governs a blockchain network. Outside of cryptocurrencies, the most common usage of hash functions is in the storage of passwords.
Let’s go back to the very basics. A mathematical function is used to illustrate an expression or a relationship involving one or more variables or sets. Consequently, a function relates an input to an output.
An example of this would be the size and price of burgers at a restaurant.
The cost of a burger is determined by its size.
Therefore, in this case, the cost is a function of the size.
Let’s say you can buy small, medium and large burgers and their respective costs are $1.50, $2.50 and $3.50.
The input is the size of the burger.
The output is the cost of the burger.
A hash function turns an input (for example text) into a string of bytes with a fixed length and structure. The output or value created is called a ‘hash value’ or ‘checksum.’ Any hash value created from data using a specific hashing algorithm is always the same length and one-way - it cannot be reversed.
New to Bitpanda? Register your account today!
Sign up hereThe term "hash function" is derived from the French word “hacher” which means to “chop into small pieces”, indicating how a hash function is designed to “chop” the data. Another type of data structure, a hash table, is frequently used for rapid detection of any two identical hashes (hash values).
After Diffie and Hellman first identified the need for a one-way hash function in their 1976 seminal paper on public-key cryptography, over the next two decades developments in cryptography progressed rapidly. In 1990, cryptographer and MIT professor, Ronald Rivest, invented the MD4 hash function and later the MD5 and MD6 functions. In 1995, the NSA (National Security Agency) designed the SHA-1 (Secure Hash Algorithm 1) based on Rivest’s design, followed by the SHA-2 update in 2001. SHA-2 is the standard that inspired SHA-256, which served as the baseline for Bitcoin’s consensus algorithm.
The purpose of hash functions
Hash functions originated from the need to make content uniform in length on one hand, and for usage as singularly unique identifiers on the other. Typical uses for hash functions outside the cryptocurrency sphere include:
Calculating a (short) checksum for an object, such as the checksum for an ISBN (International Standard Book Number)
Identifying any content almost without ambiguity but still “briefly”, without revealing anything about the content in cryptographic applications
Properties of hash functions
A cryptographic hash function should be computationally efficient, meaning that it must be quick in performance to create the hash value. It has to be deterministic - every time you put in a certain input, it has to produce the same output and to be pre-image resistant which means it cannot reveal any information about the input in the output.
Finally, a hash function has to be collision-resistant which ensures that it has to be impossible for two different inputs to produce the same output. It is the deterministic feature, pre-image resistance and collision-resistance that constitute the three most important properties of hash functions in the Bitcoin mining process.
A hash function has to be collision-resistant which ensures that it has to be impossible for two different inputs to produce the same output.
Hash functions in the mining process
Quickly running through the validation process in the Bitcoin network again, a block is bundled and contains several transactions as well as information on the previous block. This means if someone wanted to change the ledger or double-spend a transaction, he or she would have to change the hash in all previous blocks.
In order for the bundled block to be added to the blockchain, miners need to find a hash that meets the target difficulty. Each block contains a blockheader with the number of the block, the hash of the previous block and a “nonce”, which includes a timestamp. The purpose of a nonce is varying the input to a cryptographic hash function, that is increased randomness, in computation during the mining process.
Solving the hash
The node then begins “hashing” the data by converting it into the hash value or “hash”, which always needs to contain a certain number of zeros. The node checks whether a hash meets the criteria of difficulty. The hash must start with the correct amount of zeroes. If the hash meets the criteria of difficulty, it is broadcast to the other miners in the network. The first miner to find a valid hash validates the block into a new block and gets rewarded the block reward and fees in Bitcoin.
If the hash does not meet the criteria of network difficulty, another nonce is selected and hashed. Miners probably have to generate many hashes with many nonces until they find a nonce that meets the difficulty. This is the repetitive and energy-intensive process known as Bitcoin mining which requires extensive computational power.
Hash functions constitute the backbone of the Proof of Work process. Without confirmation and production of hash transactions, the blockchain would not be tamper-proof and inalterable and it would not be possible to prove who owned which amount of Bitcoin at what time.
Are you ready to buy cryptocurrencies?
Get started nowDISCLAIMER
This article does not constitute investment advice, nor is it an offer or invitation to purchase any crypto assets.
This article is for general purposes of information only and no representation or warranty, either expressed or implied, is made as to, and no reliance should be placed on, the fairness, accuracy, completeness or correctness of this article or opinions contained herein.
Some statements contained in this article may be of future expectations that are based on our current views and assumptions and involve uncertainties that could cause actual results, performance or events which differ from those statements.
None of the Bitpanda GmbH nor any of its affiliates, advisors or representatives shall have any liability whatsoever arising in connection with this article.
Please note that an investment in crypto assets carries risks in addition to the opportunities described above.